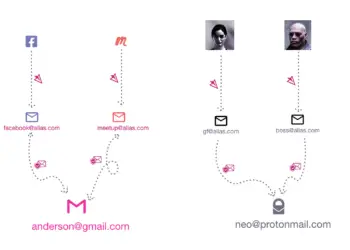
Social engineering is one of a scammer’s most cunning and effective tools. Unlike technical hacking, which often involves finding vulnerabilities in Software, social engineering exploits the human element—using deception and manipulation to trick people into giving away sensitive information or performing actions that compromise their security.
What is Social Engineering?
Social engineering is the psychological manipulation of individuals into divulging confidential information or performing actions that may lead to a security breach. This tactic leverages our natural tendencies to trust, help, and comply with authority, making it a highly effective approach for cybercriminals.
Common Social Engineering Techniques
- Phishing: This is one of the most widespread forms of social engineering. Attackers send emails or messages pretending to be from a reputable source, such as a bank or a well-known company, tricking victims into providing personal information like passwords, credit card numbers, or other sensitive data.
- Pretexting: In this scenario, the scammer creates a fabricated scenario or pretext to obtain information. For example, someone might pretend to be an IT support technician and ask for login credentials to “fix” a non-existent issue.
- Baiting: This involves leaving a physical item, like a USB drive labeled “Confidential,” in a public place. When someone picks it up and plugs it into their computer, malware is installed.
- Quid Pro Quo: Attackers offer a service or benefit in exchange for information. For instance, they pose as tech support, offering to solve a problem in exchange for login details.
- Tailgating is a physical form of social engineering where someone gains access to a restricted area by following closely behind an authorized person.
This is a recorded prank phone call, originally produced by The Jubal Show.
Disclaimer
This is a recorded prank phone call, originally produced by The Jubal Show. This recording its a good for educational purposes as part of a discussion on social engineering. While this recording is fictional and intended to raise awareness, it highlights a very real and significant threat. Every day, countless individuals are targeted by social engineering attacks, often without realizing the dangers they face. It’s crucial to remain vigilant and informed about the tactics used by scammers to protect your personal information and keep your data safe. Always verify the identity of those requesting sensitive information and think twice before sharing anything that could be used against you.
How to Protect Yourself from Social Engineering Scams
- Be Skeptical of Unsolicited Requests: Whether it’s a phone call, email, or in-person request, always be wary of unsolicited attempts to access your information or get you to act. Verify the identity of the requester independently, using official channels.
- Educate Yourself and Others: Awareness is critical. Regularly update your knowledge about the latest social engineering tactics and share this information with friends, family, and colleagues.
- Use Strong, Unique Passwords: A strong password is your first line of defense. Avoid using easily guessable information like birthdays or common words. Consider using a password manager to create and store complex passwords.
- Enable Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring your password and a second form of verification, such as a text message code or authentication app.
- Be Cautious with Personal Information: Be mindful of what you share on social media and other public platforms. Scammers can use this information to build a convincing pretext.
- Verify Before You Act: Respond if you receive a suspicious email or call. Contact the organization directly using official contact details to verify the request’s legitimacy.
- Keep Software Updated: Regularly update your operating system, browsers, and other Software to protect against known vulnerabilities that could be exploited by attackers.
- Report Suspicious Activities: If you suspect a social engineering scam has targeted you, immediately report it to your company’s IT department or relevant authorities.
Conclusion
Social engineering scams exploit our natural tendencies to trust and help others. By being aware of these tactics and taking proactive steps to secure your information, you can significantly reduce your risk of falling victim to these schemes. Remember, a healthy dose of skepticism can be your best defense in the digital world.
We at SecureCyberNetwork are dedicated to providing you with the latest updates, tips, and expert advice to keep you safe in the digital world.
Your commitment to staying informed is about your safety, the safety of your loved ones, and the safety of our community.
Your involvement is powerful.