CyberSecurity
Cybersecurity refers to the practice of protecting computers, networks, servers, mobile devices, and the data they store from malicious attacks, unauthorized access, damage, or theft. It encompasses a wide range of practices, tools, and techniques to defend digital assets from threats like hackers, malware, ransomware, and phishing schemes.
How Social Media Can Turn You Into an Insider Threat
How Social Media Can Turn You Into an Insider Threat Social media is embedded in our daily routines—personally and professionally....
MOBILE APP SECURITY IN 2025
Four keys to selecting safe mobile applications.Mobile device security will be a hot button topic for years to come. Smartphones...
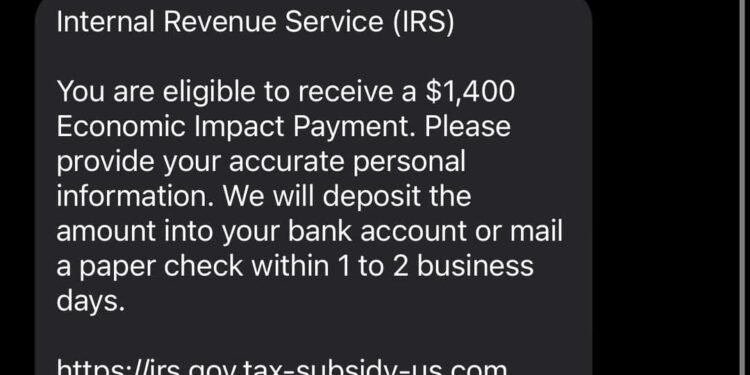
Beware of IRS Scam Text Messages
In recent weeks, we’ve seen a rise in scam text messages impersonating the Internal Revenue Service (IRS), targeting individuals by...
THREE FACTS ABOUT THE INTERNET OF THINGS (IoT)
How to adequately protect yourselfThe Internet of Things or IoT is a collective term used to describe a growing number...
Investing in Bitcoin at the Worst Time
A Life Savings Gamble on BitcoinJohn had always been curious about Bitcoin, hearing endless stories about how it had turned...
The Growing Threat of Data Breaches: A Look at the Numbers
Data leaks are becoming one of the biggest security dangers for individuals and companies in today's connected world. Unauthorized access...
2023 Scam Report: A Stark Warning for All Age Groups
As digital technology continues to advance, so do scammers' tactics, making it more critical than ever for everyone, regardless of...
Major Data Breach Confirmed by National Public Data, Exposing Millions of Americans’ Personal Information
A massive data breach has been confirmed by National Public Data, a company that aggregates information for background checks. The...
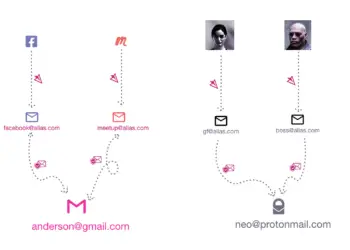
Understanding Social Engineering: Protect Yourself from Scams
Social engineering is one of a scammer's most cunning and effective tools. Unlike technical hacking, which often involves finding vulnerabilities...
Securing a Strong Password: Essential Tips for Fraud Prevention + Password Generator
In today's digital age, securing your online accounts is more crucial than ever. A strong password is one of the...